
Intelligent Integration
Intelligent Content Integration. What is it and why is it Important?
We are consistently hearing from our customers about the tremendous stresses being placed on their workforces stemming from historic low unemployment rates coupled with an aging workforce resulting in difficulties finding and retaining knowledge worker talent. Turnover creates an ongoing training effort which is compounded by ever changing business requirements and policy changes making standard operating procedures anything but standard. It is easy to see how these stresses can lead to workforce productivity and information quality issues.
Automate Standard Operating Procedures and Pivot to Self Service
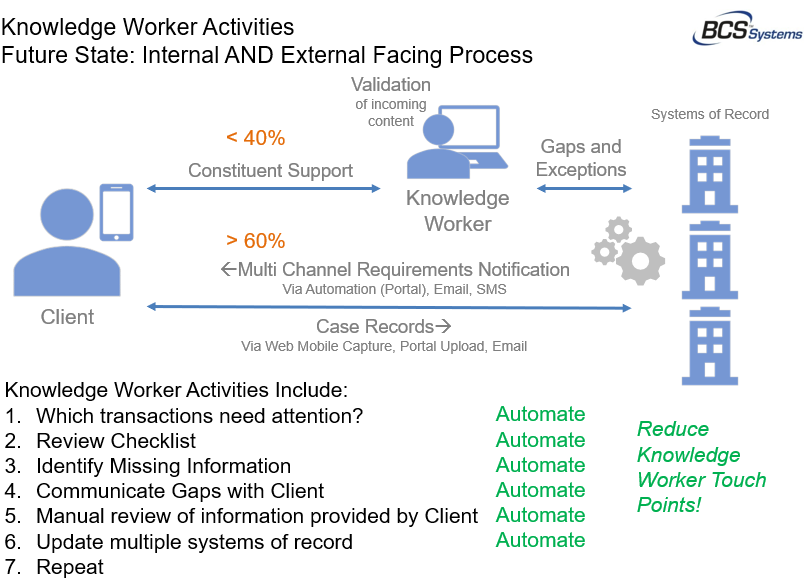
Every mission-critical business process is, or should be, defined by a standard operating procedure (SOP), a set of instructions used as an operational guideline for transaction requirements. With our solutions in place, the technology looks at all transactions in the business process and automatically identify the information gaps. The gaps are communicated to the knowledge worker or even to the client in the form of emails or text notifications allowing activities to be focused on the completion of missing information.
iConnect can direct knowledge workers to focus on transactions requiring attention while automating mundane tasks of filling gaps in case or transaction records.
Integrate Content Using API Security
While there are many integration platforms in the market, iConnect is the clear choice for integrating enterprise content to business applications. Application Programming Interfaces (API’s) are used to integrate disparate applications and to exchange data between them. Unsecure API’s can contain vulnerabilities that may expose your organization to data breaches. API security is essential to reducing the possibility of this occurrence. The BCS iConnect API has been designed from the ground up to provide a zero-trust information security framework. By utilizing our zero trust REST API to build integrations between applications, you can reduce your vulnerability to attacks and breaches.